How Network Security Works: Protocols, Tools, and Detection Explained
In today’s digital age, where almost every business and personal activity is connected online, network security has become a crucial layer of protection. Whether it’s financial transactions, email communication, or cloud data storage, cybercriminals are always on the lookout for vulnerabilities. So, how exactly does network security work? Let’s dive deep into the mechanisms, protocols, and tools that keep your data and networks safe.
What Is Network Security?
Network security refers to the policies, procedures, and technologies used to protect the integrity, confidentiality, and accessibility of computer networks and data. It involves multiple layers of defence spread across the network, including both hardware and software solutions.
Effective network security manages access to the network, monitors traffic, detects threats, and blocks malicious activities before damage can occur.
Why Is Network Security Important?
Network security is essential for:
- Protecting sensitive data (financial, medical, personal)
- Preventing unauthorised access
- Maintaining business continuity
- Complying with regulations (like GDPR, HIPAA, etc.)
- Mitigating financial and reputational losses
Cyberattacks are becoming more advanced and frequent. From ransomware to phishing, the risks are real—and the need for robust network security has never been greater.
What Are Network Security Protocols?
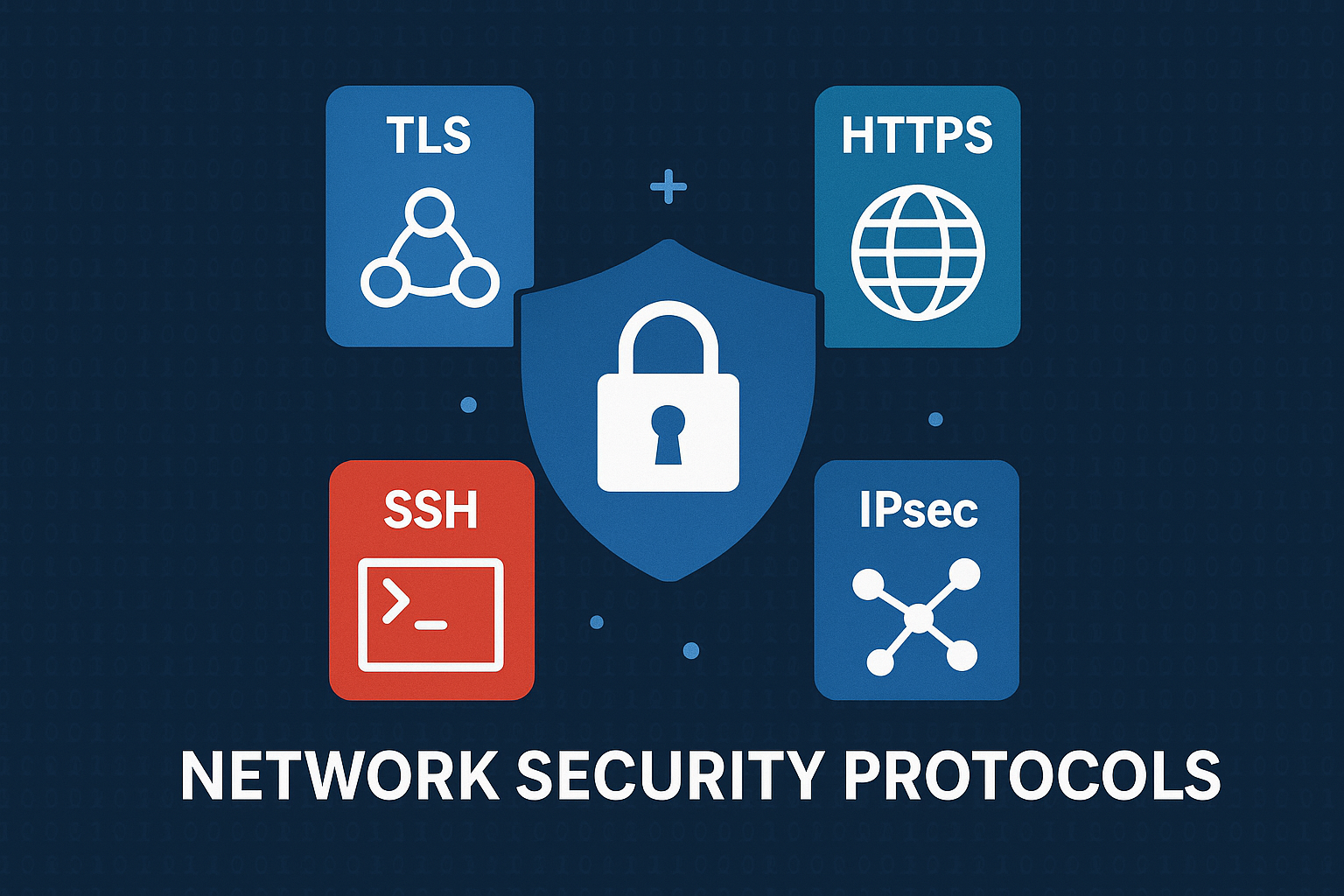
Network security protocols are standardized rules and instructions designed to protect data as it moves across or within networks. These protocols ensure secure communication between devices and networks, making sure that data remains intact, confidential, and accessible only to authorised users.
Here are some of the most commonly used network security protocols:
SSL/TLS (Secure Sockets Layer/Transport Layer Security)
SSL and its successor TLS are cryptographic protocols that provide secure communication over the internet. They encrypt the data between your browser and the server, ensuring that third parties can’t read or modify it.
Use case: Secure websites (HTTPS), emails, and messaging apps.
IPSec (Internet Protocol Security)
IPSec is a suite of protocols used to secure Internet Protocol (IP) communications by authenticating and encrypting each IP packet during the communication session.
Use case: VPNs (Virtual Private Networks), site-to-site encryption.
HTTPS (Hypertext Transfer Protocol Secure)
HTTPS is essentially HTTP wrapped with SSL/TLS. It provides a secure channel for browsing websites.
Use case: E-commerce sites, online banking, form submissions.
SSH (Secure Shell)
SSH is used to securely log into remote systems and execute commands over an unsecured network.
Use case: Secure remote server management, file transfers (using SFTP).
Kerberos
Kerberos is an authentication protocol that uses tickets to allow nodes to prove their identity over a non-secure network.
Use case: Secure authentication in enterprise environments like Windows Active Directory.
RADIUS and TACACS+
These are protocols used for centralised Authentication, Authorization, and Accounting (AAA) of users who connect and use a network service.
Use case: Corporate networks, remote access servers.
These protocols work together to build layers of defence against eavesdropping, spoofing, and unauthorised access.
Which Network Security Tool Can Detect Threats?

Network threats are increasingly stealthy, fast-moving, and complex. That’s where network security tools come in. These tools detect, monitor, and respond to suspicious activity in real-time.
Here are some of the top network security tools used for threat detection:
1. Intrusion Detection System (IDS)
An IDS monitors network traffic for suspicious patterns or anomalies. It alerts administrators when it detects potential malicious activity.
Example tools: Snort, Suricata, OSSEC
Detection capabilities: Port scans, malware signatures, brute force attacks
2. Intrusion Prevention System (IPS)

While IDS only detects and alerts, an IPS goes one step further by automatically taking actions such as blocking IP addresses or dropping malicious packets.
Example tools: Cisco Firepower, Palo Alto Networks IPS
Detection capabilities: Real-time packet inspection, threat prevention
3. Security Information and Event Management (SIEM)
SIEM tools collect and analyse data from various sources across the network. They help identify security threats, investigate incidents, and support compliance.
Example tools: Splunk, IBM QRadar, SolarWinds
Detection capabilities: Log analysis, behavioural analytics, anomaly detection
4. Network Traffic Analysis (NTA) Tools
NTA tools monitor network traffic and detect unusual patterns that may indicate threats.
Example tools: Darktrace, Vectra AI, Corelight
Detection capabilities: Zero-day attacks, insider threats, lateral movement
5. Endpoint Detection and Response (EDR)
Although focused on endpoints like laptops and desktops, EDR tools play a vital role in detecting how a threat moves across a network.
Example tools: CrowdStrike Falcon, Microsoft Defender for Endpoint
Detection capabilities: Malware, ransomware, data exfiltration
6. Firewall
Modern firewalls are intelligent and come with threat detection capabilities such as Deep Packet Inspection (DPI), which can analyse network packets for malicious activity.
Example tools: Fortinet, Check Point, SonicWall
Detection capabilities: Botnets, phishing sites, command & control traffic
Best Practices for Strong Network Security
Here are some practical steps to enhance your network security posture:
- Use multi-factor authentication (MFA)
- Update and patch systems regularly
- Encrypt sensitive data
- Segment your network
- Deploy antivirus and anti-malware tools
- Educate employees about cybersecurity awareness
- Perform regular vulnerability assessments
Mechsoft is a Trusted Network Security Provider in the UAE
Mechsoft is a trusted network security provider in the UAE, offering advanced solutions to protect businesses from cyber threats. With a focus on secure infrastructure, threat detection, and compliance, Mechsoft helps organisations safeguard their data and networks.
From firewalls to intrusion prevention systems, they deliver reliable, scalable, and customised cybersecurity services across various industries.