Leading Security Operations Centre (SOC) service in Dubai, UAE, providing top-tier security monitoring and threat detection services. Our expert team leverages advanced technologies to deliver 24/7 protection for your business. We specialize in proactive incident response, vulnerability management, and continuous security enhancement, ensuring your organization’s safety in the dynamic UAE landscape.
Mechsoft Technologies’ 24×7 SOC-as-a-Service, together with cutting-edge threat intelligence and knowledgeable defenders, will help you defend against the most complex threats.
The Security Operations Centre (SOC) is a crucial cybersecurity service offered by Mechsoft Technologies in Dubai, UAE. Essentially, a SOC is a dedicated cybersecurity facility equipped with a specialized team and advanced tools to continuously monitor and defend your digital assets against cyber threats, 24/7.
Investing in a SOC is one of the most reliable ways companies can safeguard against financial losses due to unexpected attacks or data breaches. With around-the-clock monitoring by a team of expert ethical hackers, your business can maintain its financial stability and protect its reputation.
Mechsoft SOC as a Service delivers all of the benefits of a dedicated 24/7 SOC, but without the high costs, complexity, and frustrations that come with building, staffing, and managing one in-house.
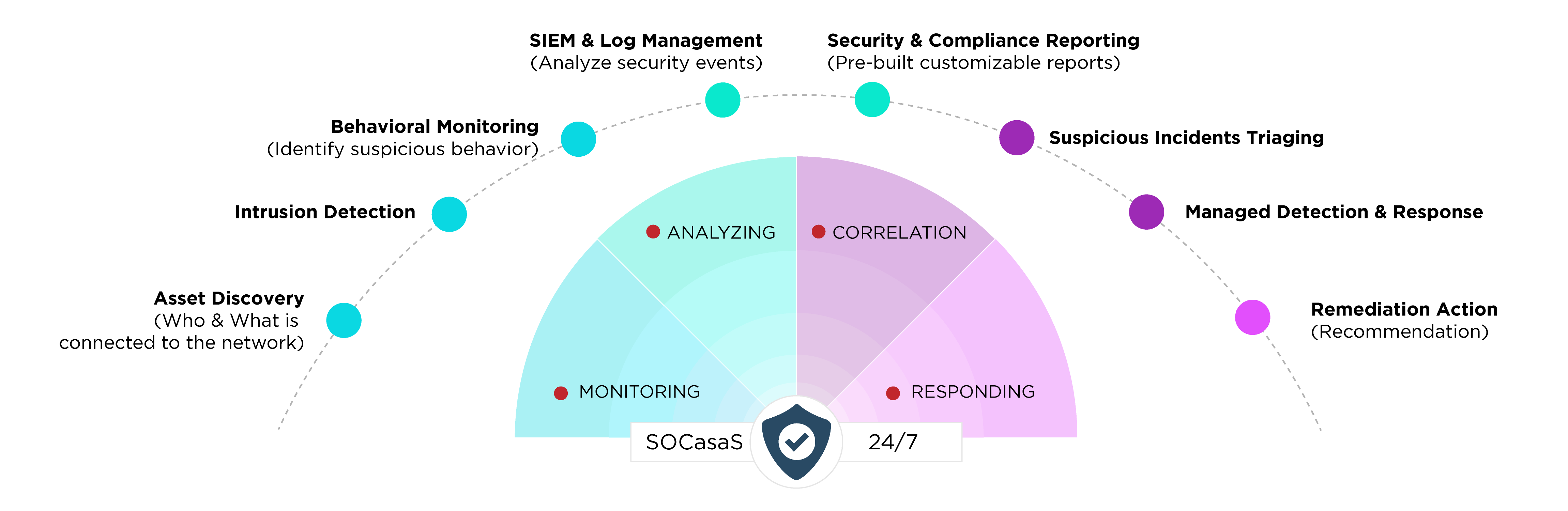
Get a comprehensive cyber security model, including Managed Detection and Response (MDR), SIEM capabilities, SOC experts, etc., to secure your business. With the effective combination of people, products, and processes, we can help detect advanced threats and contain them before they impact your business.
The SOC team consists of 3 different tiers of SOC analysts and dedicated managers.
Tier 1 analysts are mainly responsible for collecting raw data as well as reviewing alarms and alerts. They need to confirm, determine, or adjust the criticality of alerts. They also enrich them with relevant data.
For every alert, the triage specialist has to identify whether it’s justified or a false positive. Alert fatigue is a real issue.If tier 1 analysts cannot solve occurring problems, they must escalate them to tier 2 analysts.
At tier 2, analysts review higher-priority security incidents. Triage specialists escalate these incidents. They perform a more in-depth assessment using threat intelligence. They need to understand the scope of an attack and be aware of the affected systems.
This second tier transforms the raw attack telemetry data collected at tier 1. It turns it into actionable threat intelligence. Incident responders design and implement strategies to contain and recover from an incident. They are responsible for this.
If a tier 2 analyst faces major challenges in identifying or mitigating an attack, they consult other tier 2 analysts. If necessary, they escalate the incident to tier 3.
Tier 3 analysts are the most experienced workforce in a SOC. They handle major incidents escalated to them by the incident responders. They also perform or at least supervise vulnerability assessments. They conduct penetration tests to identify possible attack vectors.
Their most important responsibility is to proactively identify possible threats, security gaps, and vulnerabilities. These may be unknown.
They should also recommend ways to optimize the deployed security monitoring tools. They can do this as they gain reasonable knowledge about possible threat detection to the systems.
SOC managers supervise the security operations team. They provide technical guidance if needed, but most importantly, they are in charge of adequately managing the team.
This includes hiring, training and evaluating team members; creating processes; assessing incident reports; and developing and implementing necessary crisis communication plans.
They also oversee the financial aspects of a SOC, support security audits, and report to the chief information security officer (CISO) or a respective top-level management position.
A Security Operations Center (SOC) as a service encompasses the personnel, processes, and technologies essential for monitoring, analyzing, and safeguarding an organization’s information security. Serving as the company’s intelligence hub, the SOC collects real-time data from networks, servers, endpoints, and other digital assets, leveraging intelligent automation to detect, prioritize, and respond to potential cybersecurity threats.
In the past, SOC infrastructure was considered a heavy investment, affordable only for large or highly security-conscious organizations. However, advancements in collaboration tools and security technologies have enabled many enterprises to implement virtual SOC processes and technologies. These solutions do not require a dedicated facility and can be managed by part-time security, operations, and development personnel.
Furthermore, many organizations are adopting managed SOC infrastructures or hybrid SOCs, which blend in-house resources with the tools and expertise of Managed Security Service Providers (MSSPs). Managed SOC solutions offer enhanced visibility, automation, and security expertise, significantly improving an organization’s overall security posture by enabling rapid threat detection and incident response.
In today’s digital era, the growing ambitions of companies in their digital transformation journeys have made cybersecurity and data privacy more crucial than ever. According to PwC, 42% of CEOs recognize cyber and data privacy as key areas that significantly impact companies as they advance their digital initiatives. However, the benefits of digital transformation come with heightened risks, particularly the increased threat of intrusions and cyberattacks on digital infrastructures.
The global rise in cyberattacks underscores the urgency for robust cybersecurity measures. A Kaspersky study revealed a staggering 190% increase in cyberattacks since the onset of the pandemic in March 2020. These attacks not only cause financial losses for businesses and their customers but also damage trust, leading to reputational, legal, financial, and regulatory consequences.
In this challenging environment, businesses are compelled to adopt proactive defense strategies. While completely preventing cyberattacks is impossible, organizations must be equipped with the right technology and processes to anticipate, detect, mitigate, and recover from incidents. These critical functions are centralized within a Security Operations Center (SOC) as a service.
Acknowledging the growing need to counter cyber threats, Finesse has introduced its cutting-edge Cognitive Security Operations Center (CSOC), which operates 24/7. Designed specifically for business clients, our state-of-the-art SOC provides a cost-effective solution to protect their digital infrastructure against the increasing threat landscape of cyberattacks
© 2025 Mechsoft Technologies. All Rights Reserved.