Table of Contents
An insider threat is a type of cyber security risk within an organization. This risk often arises when someone like an employee, contractor, vendor, or partner, who has legitimate access, misuses that access in a way that harms the organization’s networks, systems, and data. Whether done on purpose or by accident, the outcome is the same: the confidentiality, availability, and integrity of the organization’s systems and data are put at risk.
Most data breaches can be traced back through insider threat monitoring system. Traditional cyber security measures tend to focus more on external dangers, leaving a gap in defense against internal attacks. The challenge here is that insiders already have authorized access to data and systems, making it tough for security experts and tools to tell apart normal activities from harmful ones.
Types of Insider Threat
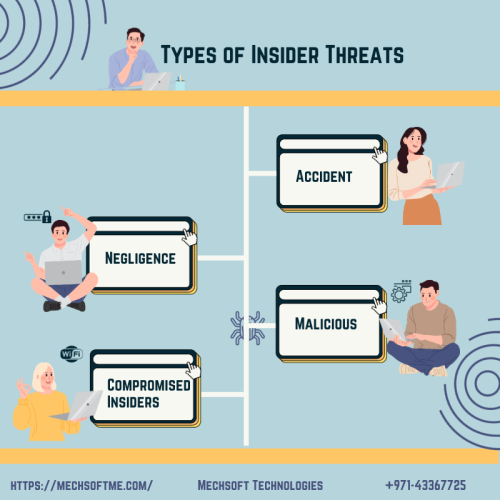
Accident
Accidental insider threats pose a risk to cyber security, often due to a lack of awareness about security policies or simple errors in their daily tasks.
For instance, such threats can occur when someone accidentally sends sensitive information to the wrong person, misplaces a device holding confidential data, or unknowingly downloads malware onto a company device.
Negligence
Negligent insiders, though not intentionally harmful, can still pose security risks due to their lack of awareness or careless actions. Examples of this include succumbing to phishing scams, skirting security measures for convenience, misplacing a laptop that then falls into cybercriminals’ hands, or mistakenly sending emails with sensitive files to people outside the organization.
For example, In the current hybrid work setting, a concerning 64 percent of employees use personal devices for work tasks without adequate security, making careless insiders a major threat to cyber security and data privacy.
Additionally, with more than a third of employees not regularly updating their passwords, there’s an increased chance of threat actors taking advantage of this negligence to access company accounts and networks.
Malicious
Malicious insiders often include current employees who are unhappy, or former employees whose access hasn’t been revoked, deliberately misusing their access for revenge, financial gain, or both. Some of these insiders might collaborate with external malicious parties, like hackers, competitors, or agents of foreign states.
Their aim could be to disrupt business operations by planting malware or tampering with files or applications, or to leak sensitive information such as customer details, intellectual property, trade secrets, or other confidential data.
For Example, In 2022, a Twitter employee was apprehended for sharing private information of Twitter users with representatives of the Kingdom of Saudi Arabia and the Saudi Royal family, in return for bribes. As per the U.S. Department of Justice, this employee covertly functioned as an agent for a foreign government, aiming at those who voiced dissent.
Compromised Insiders
Compromised insiders are authentic users whose access credentials have been hijacked by external threat actors. Incidents involving these compromised insiders rank as the costliest types of insider threats.
For instance, in 2021, a scammer employed a social engineering strategy, particularly a voice phishing (vishing) phone call, to acquire access credentials to the customer support systems of the trading platform Robinhood. This attack led to the theft of over 5 million customer email addresses and 2 million names.
How Insider Threats Can Affect Your Companies Productivity and Security?
Insider threats are a major cyber security risk that can have a devastating impact on organizations. These threats can range from accidental or intentional misplacement of confidential information to sabotaging critical systems, leading to lost productivity, financial losses, and reputational damage. To mitigate this risk, organizations need to implement a comprehensive cyber security strategy that includes employee behaviour analytics, strong access controls, data loss prevention solutions, user education and training, and continuous monitoring.
Types of Insider Threats Threatening Productivity
Disengaged Employees
Studies have revealed ample scientific evidence that indicate a decline in employee engagement in organizations. Employees end up performing jobs and tasks they were not hired for.
Like for example the sales team may be stuck in administrative tasks and customer service might be spending hours in spreadsheets tracking performance data. Having an activity monitoring tools can help organizations quickly spot such inefficiencies that lead to disengagements and allow for workflow optimization.
These tools can identify idle time, and unproductive activity and even perform psycholinguistic analysis to identify signs of negative sentiments.
Employee Burnout
Employee burnout is a widespread issue in today’s work environment. A Qualtrics report indicates that in the UAE, 36% of employees experience burnout, and 43% feel emotionally drained by their work.
The causes are complex, with many employees struggling to handle increasing workloads, manage stress effectively, and maintain connections with colleagues and leaders.
Quiet Quitting
Quiet Quitting varies in meaning for different individuals, but it typically involves employees establishing firmer boundaries by sticking strictly to their official job roles.
This form of quitting can adversely affect the workplace, potentially resulting in reduced productivity, loss of valuable organizational knowledge, and an increased workload for the remaining staff.
Insider Threat Detection Solutions By Mechsoft Technologies
Mechsoft Technologies offers a specialized suite of services tailored to address the unique challenges posed by insider threats. Our innovative approach integrates advanced analytics, machine learning, and user behavior analytics to both detect and mitigate risks arising from insider activities.
The tools we provide are specifically designed to safeguard against data breaches, intellectual property theft, and other malicious actions by employees. This includes features such as real-time monitoring, incident response, and predictive risk scoring, ensuring that your organization remains proactive in mitigating potential threats.
Connect with our experts to gain further insights into how our insider threat solutions can help you identify threats before breaches occur, respond promptly, and ultimately reduce the costs associated with remediation.