Table of Contents
In the fast-paced world of cybersecurity, the threat landscape is continually shifting. Safeguarding against potential cyberattacks necessitates swift monitoring and response capabilities. Timely intervention is crucial because the longer a cyber security incident persists without remediation, the higher the potential for extensive damage and increased costs for the organisation.
Security Operations Center (SOC) is a pivotal entity entrusted with the responsibility of countering these evolving threats. A well-equipped SOC stands as a vigilant guardian, offering round-the-clock surveillance against cyber threats and has the ability to engage in decisive incident response.
What is a Security Operations Center (SOC)?
A Security Operations Center, or SOC, functions as a central hub for a company’s cybersecurity efforts. Imagine it as a dedicated team of experts, state-of-the-art technology, and streamlined processes working in unison to fortify the digital defences of your organisation.
The SOC operates around the clock, diligently monitoring for potential cyber threats and swiftly responding to any incidents that may arise. Its primary role is not just to identify risks but also to orchestrate timely and effective countermeasures.
In essence, the SOC serves as a vigilant guardian, ensuring the resilience and security of your organisation’s information infrastructure amidst the ever-evolving landscape of cyber threats.
What are the functions of a Security Operations Center?
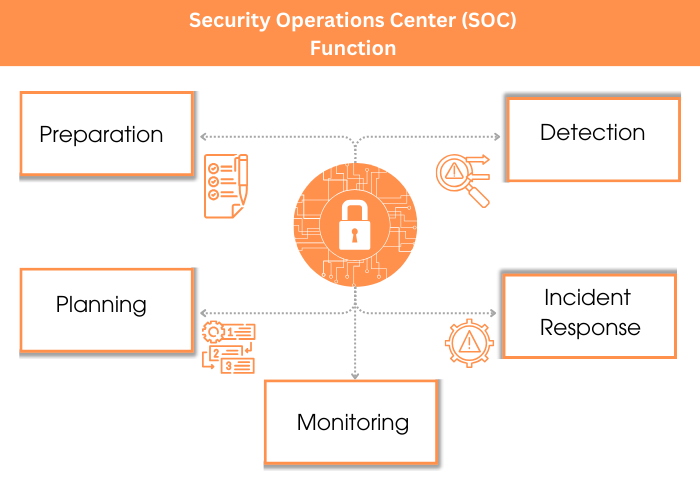
The SOC team handles the continuous operational tasks related to the security of an enterprise’s network and infrastructure.
Although members of the security operations team can provide insights or expertise in formulating security strategies or in the design of security architecture, the primary role of a SOC team is centred on detecting, analysing, investigating, remedying, and responding to security incidents and threats.
ALSO READ: WHAT IS SOC AS A SERVICE(SOCAAS)?
Functions of Security Operations Center:
Preparation: To ensure that security tools and measures are as effective as possible, the SOC carries out preventive maintenance tasks. These include applying software patches and upgrades, regularly updating firewalls, whitelists, blacklists, and revising security policies and procedures.
Incident response planning: The SOC holds the responsibility for creating the organisation’s incident response strategy. This includes conducting vulnerability assessments, which are thorough evaluations identifying the susceptibility of each resource to potential threats and associated costs.
Additionally, the SOC team carries out penetration tests, mimicking specific attacks on one or more systems. Based on the outcomes of these tests, the team then refines or corrects applications, security policies, best practices, and incident response plans.
Monitoring: The principal technology for monitoring, detection, and response has traditionally been Security Information and Event Management (SIEM).
SIEM functions by monitoring and gathering alerts and telemetry from network software and hardware in real-time, then analysing this data to pinpoint possible threats.
Detection: The SOC team distinguishes genuine cyber threats and hacker exploits from false alarms, sorting meaningful signals from irrelevant noise. They then prioritise these threats based on their severity.
Contemporary SIEM solutions incorporate artificial intelligence (AI) that not only automates these tasks but also improves at identifying suspicious activities over time by ‘learning’ from the data.
Incident Response: SOC limits the damage by taking the following action.
- Investigating the root cause to identify the technical vulnerabilities that allowed hackers access to the system, along with other contributing factors like weak password practices or lax policy enforcement.
- Turning off or detaching compromised endpoints from the network.
- Segmenting affected parts of the network or redirecting network traffic.
- Halting or terminating compromised applications or processes.
- Removing damaged or infected files.
- Executing antivirus or anti-malware scans.
- Revoking passwords for both internal and external users.
Key Role of SOC Team
SOC Manager: Oversee the SOC Team, handle all security operations, and report to the organisation’s Chief Information Security Officer (CISO).
Security Engineers: Oversee the organisation’s security architecture. This role largely entails assessing, trialling, endorsing, implementing, and sustaining various security tools and technologies.
Security Analysts: First responders to cybersecurity threats or incidents. Analysts detect, investigate, and triage (prioritise) threats; then they identify the impacted hosts, endpoints, and users, and take the appropriate actions to mitigate and contain the impact or the threat or incident.
Benefits of Working with Mechsoft Technologies as a SOC-as-a-Service (SOCaaS) Provider.
Outsourcing SOC tasks to a specialised Managed Security Service Provider (MSSP) like Mechsoft Technologies, provides distinct and economically advantageous benefits compared to managing a SOC internally.
Mechsoft Technologies, based in Dubai, has established itself as a prominent SOC-as-a-service provider in Dubai. They offer a comprehensive suite of cybersecurity solutions, tailored to protect against the region’s unique digital threats.
Their 24/7 Security Operations Center is staffed by expert security professionals, equipped with advanced tools and technologies. Schedule a call with them to learn more about cyber security services.
Mechsoft Technologies’ commitment to excellence in security operations makes it a trusted partner for organisations seeking robust cyber defence in the Middle East.



