Table of Contents
Penetration testing is like a mock cyberattack aimed at pinpointing weak spots and figuring out how to get around security defenses. Catching these issues early lets security teams patch things up, heading off data breaches that might lead to massive financial hits.
Pen tests are also key for checking if a company is following the rules, getting employees up to speed on security practices, seeing how well plans for dealing with incidents work, and making sure the business can keep running smoothly.
Companies can take what they learn from a penetration test to strengthen their systems before any real cyber threats strike. Penetration testing is a vital part of cybersecurity in all kinds of industries, and there’s a big market for skilled penetration testers.
Types of Penetration Testing
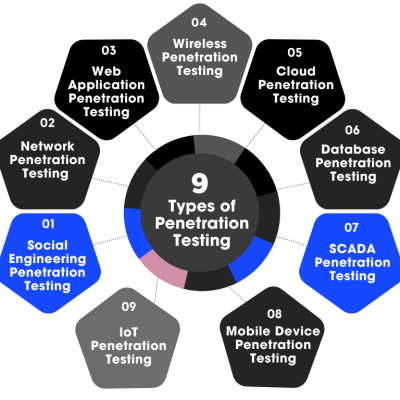
Social Engineering Penetration Testing
In a social engineering test, the goal is to see if employees can be persuaded to reveal confidential information or grant access to the organization’s systems. This exercise helps penetration testers gauge how susceptible the organization is to deception and various types of social engineering cyber threats.
Network Penetration Testing (Internal, External, and Perimeter Devices)
Network penetration tests are split into two types: external and internal.
With the growing use of cloud services and IoT devices, the boundaries of network perimeters may not be as clear-cut as before, yet they remain an essential defense layer. Conducting routine penetration tests on perimeter devices like remote servers, routers, desktops, and firewalls is crucial for spotting potential security breaches and vulnerabilities.
Web Application Penetration Testing
Web application penetration testing is carried out to find security gaps in web applications, websites, and web services. Pen testers examine the security of the coding, any flaws in the application’s security measures, and the overall design.
This approach to pen testing helps businesses fulfill compliance obligations and evaluate the security of exposed elements such as firewalls, DNS servers, and routers. Given that web applications frequently receive updates, it’s vital to regularly scan these apps for new vulnerabilities and devise plans to counter possible risks.
Wireless Penetration Testing
As wireless technology becomes almost universal, it’s important for businesses to spot, evaluate, and protect their wireless setups. Wireless penetration testing uncovers security weaknesses in wireless access points, including WiFi networks and devices. Testers search for issues such as poor encryption, Bluetooth vulnerabilities, authentication attacks, and harmful wireless devices to help prevent data leaks.
Cloud Penetration Testing
As cloud computing turns into a key factor for business growth, companies need to strengthen their cloud technology security to prevent cyber threats. Cloud penetration testing is conducted to discover weak spots in cloud environments. These tests offer insights into the robustness and vulnerabilities of cloud security solutions, improve incident response strategies, and help avert potential breaches.
Database Penetration Testing
Database security is critical for organizations since attackers often aim to infiltrate databases to extract sensitive data. Database penetration testing evaluates who has access privileges to the database. Pen testers work to gain entry to your database, pinpoint access points, and then provide guidance on securing your database against potential breaches.
SCADA Penetration Testing
Supervisory Control and Data Acquisition (SCADA) systems manage, monitor, and control industrial operations and essential equipment. SCADA penetration testing is a practical way to protect these systems from outside threats. It provides a thorough assessment of possible risks and security loopholes.
Mobile Device Penetration Testing
With the vast array of mobile applications out there, they’ve become a prime target for malicious entities. Penetration testing for mobile devices is crucial for maintaining strong security. It evaluates the security level of mobile devices and their apps, uncovers vulnerabilities, and detects any coding flaws.
IoT Penetration Testing
IoT penetration testing enables specialists to find security flaws within the constantly growing IoT landscape. This technique is key to ensuring security readiness by detecting and correcting misconfigurations, thus safeguarding the IoT environment. It’s not just about avoiding security incidents; it also supports compliance with regulations and reduces the chance of operational interruptions.
Also Read: What Is The Difference Between VA & PT?
5 Steps of Penetration Testing
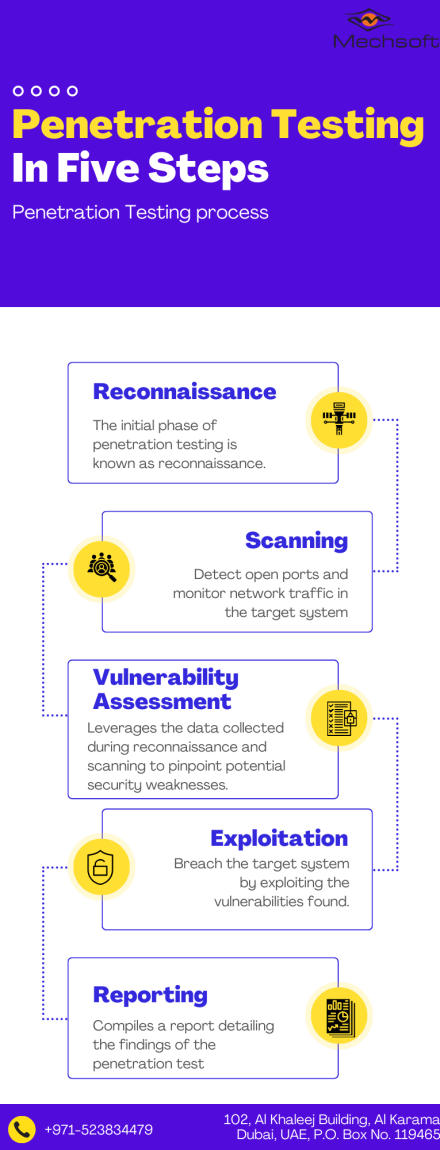
Penetration testing involves 5 key steps: gathering intelligence, scanning, assessing vulnerabilities, exploiting them, and then compiling a report. Let’s delve into each of these stages in more detail.
Reconnaissance
The initial phase of penetration testing is known as reconnaissance. During this stage, the tester collects extensive information on the target system, such as details on network structures, operating systems, applications, user accounts, and other pertinent data. The objective is to amass a wealth of information to devise an effective attack strategy.
Scanning
After collecting the necessary information in the reconnaissance phase, the next step is scanning. In this stage of penetration testing, the tester employs a range of tools to detect open ports and monitor network traffic in the target system.
Open ports can serve as gateways for attackers, so it’s crucial for penetration testers to identify as many as possible to prepare for subsequent phases of testing.
Scanning can also be a standalone process outside of penetration testing, commonly known as vulnerability scanning, which is often automated. However, for scanning to be truly effective in cybersecurity, it requires the expertise of penetration testers to maximize its effectiveness.
Vulnerability Assessment
The third stage of penetration testing is the vulnerability assessment. Here, the tester leverages the data collected during reconnaissance and scanning to pinpoint potential security weaknesses and assess if they can be exploited. While vulnerability assessment is beneficial as a standalone process, its effectiveness is significantly enhanced when integrated with the other stages of penetration testing.
Exploitation
After identifying vulnerabilities, the next step is exploitation. In this critical phase of penetration testing, the tester tries to breach the target system by exploiting the vulnerabilities found. Tools used to emulate actual attacks.
This phase is particularly sensitive, as it involves navigating past security measures to gain access to the target system.
Reporting
After completing the exploitation phase, the tester compiles a report detailing the findings of the penetration test. This report, produced in the final phase of penetration testing, serves as a guide to address the discovered vulnerabilities and to enhance the security stance of the organization.
What Occurs Following a Penetration Test?
The outcomes of a penetration test are typically condensed and examined in a report, assisting organizations in measuring security risks and developing remedial strategies. These reports offer an in-depth analysis of a network’s vulnerabilities, allowing businesses to address weaknesses and fortify their defenses, especially if it’s found that a network has been breached.
Creating a penetration testing report involves meticulously recording vulnerabilities and contextualizing them so that the organization can effectively address its security challenges.
The most informative reports contain sections that provide a detailed account of the vulnerabilities found, an assessment of the impact on the business, an evaluation of how challenging the exploitation phase was, a briefing on the technical risks, guidance on remediation, and strategic recommendations for moving forward.
4 Benefits of Penetration Testing
In the digital realm, not knowing your vulnerabilities can be both expensive and risky. Penetration testing offers vital, actionable insights that enable businesses to outpace hackers. Here’s a look at how pen testing can bolster your security measures:
Adherence to Compliance Requirements
Penetration testing aids organizations in complying with regulatory standards like PCI DSS, EU GDPR, and ISO 27001. A survey showed that 61% of security chiefs cited compliance requirements as a reason for carrying out pen tests.
Identify and Remediate Vulnerabilities
Penetration tests uncover weaknesses that could be exploited by adversaries, allowing security teams to fix them. Pen testers provide in-depth analysis of the vulnerabilities within an IT setup and suggest measures to improve security. A report indicates that 70% of organizations conduct pen tests to support their vulnerability management programs.
Ensure Business Continuity
The financial hit a company can take in the event of a data breach can be huge, not to mention the disruption to its operations. Through penetration testing, businesses can get a clearer view of potential risks, aiding in damage control.
Enhance Customer Trust
Data breaches can diminish customer confidence and potentially harm a company’s reputation. Penetration testing reduces the likelihood of attacks and provides assurance to clients.
Responsibilities of a Penetration Tester
- Carry out threat analysis on apps, network devices, and cloud systems.
- Execute security evaluations.
- Regularly test systems.
- Evaluate the strength of security protocols.
- Develop, apply, and uphold security measures.
- Set up and manage security frameworks.
- Draft, assess, and refresh information security guidelines.
- Formulate plans for business continuity and disaster recovery.
- Offer advice to address and patch up detected security shortcomings.
- Record results and report them clearly and succinctly.
Mechsoft Technologies, a reliable provider of penetration testing services in Dubai, offers comprehensive security assessments to identify and address vulnerabilities within IT infrastructures.
Our seasoned engineers are primed to handle any cybersecurity challenge. We collaborate with global cyber security leaders to deliver cutting-edge solutions and services. Feel free to reach out to our experts for a friendly chat, cyber security consultation, demo, or a free trial, and let us safeguard your digital assets.



