Table of Contents
What is Privileged Access Management?
control and monitor access to critical systems and data. It focuses on managing privileged accounts, which are accounts with elevated permissions that can access sensitive information and perform administrative tasks.
By implementing PAM, organizations can reduce the risks associated with privileged accounts, such as insider threats, data breaches, and unauthorized access. PAM solutions typically include features like password management, access control, session monitoring, and privilege elevation.
What Are Privileges and How Are They Created?
Privileges refer to the elevated permissions granted to certain accounts within a system or network. These permissions allow users to access sensitive information, perform administrative tasks, and make changes that regular users cannot.
Privileges are created by system administrators or IT personnel who assign specific access rights to individual accounts based on their roles and responsibilities within the organization. It is essential to carefully manage and monitor these privileges to prevent unauthorized access and reduce the risks associated with privileged accounts.
What are Privileged Accounts?
Privileged accounts are user accounts with elevated permissions that allow users to access sensitive information, perform administrative tasks, and make changes that regular user accounts cannot. These accounts are typically used by system administrators, IT personnel, and other authorized individuals who require elevated access to critical systems and data.
Privileged accounts are a common target for cyber attackers due to the extensive access they provide, making them a significant security risk for organizations. Proper management and monitoring of privileged accounts are essential to prevent unauthorized access and reduce the risks associated with these accounts.
Types of Privileged Accounts
Types of Privileged Accounts can vary depending on the organization and its specific needs. Some common types include
Root Accounts: These are superuser accounts with unrestricted access to all files and commands on a system. Root accounts have the highest level of privileges and are typically used for system administration tasks.
Administrator Accounts: These accounts have elevated permissions within a specific domain or system. They are often used to manage network resources, install software, and configure settings.
Service Accounts: These accounts are used by services or applications to interact with other systems or services. They often have specific permissions to perform automated tasks without human intervention.
Database Accounts: These accounts have privileged access to databases and are used to manage, query, and update database information. They are crucial for database administrators to perform their duties effectively.
Application Accounts: These accounts are used by applications to access resources or databases. They have specific permissions tailored to the needs of the application they serve.
By categorizing and managing these types of privileged accounts effectively, organizations can enhance security, reduce the risks associated with unauthorized access, and ensure proper monitoring of critical systems and data.
What are Privileged Credentials?
Privileged Credentials are the usernames and passwords associated with privileged accounts that grant users elevated access to critical systems and data.
These credentials are crucial for accessing sensitive information, performing administrative tasks, and making changes that regular user accounts cannot. Proper management of privileged credentials is essential to prevent unauthorized access and enhance security within an organization.
Need of PAM in an Organization
Privileged Access Management (PAM) is needed to help organizations control and monitor access to critical systems and data. PAM solutions play a crucial role in reducing the risks associated with privileged accounts, such as insider threats, data breaches, and unauthorized access.
By implementing PAM, organizations can enhance security, prevent unauthorized access, and ensure proper monitoring of privileged accounts, ultimately safeguarding sensitive information and critical systems.
Benefits of Privileged Access Management
Privileged Access Management (PAM) offers several benefits to organizations, including enhanced security, improved compliance, and better control over access to critical systems and data. By implementing PAM solutions, organizations can effectively reduce the risks associated with privileged accounts, such as insider threats, data breaches, and unauthorized access.
PAM helps in enforcing least privilege access, ensuring that users have only the necessary permissions to perform their tasks, thus minimizing the potential impact of security incidents.
Additionally, PAM solutions provide features like password management, access control, session monitoring, and privilege elevation, which further strengthen the organization’s security posture.
Privileged Access Management Best Practices
Privileged Access Management (PAM) best practices are essential for organizations to effectively manage and secure their privileged accounts. Some key best practices include:
Implement Least Privilege Principle: Grant users the minimum level of access required to perform their tasks. This helps reduce the risk of unauthorized access and limits the potential impact of security incidents.
Regularly Review and Update Access Rights: Conduct periodic reviews of access rights to ensure that users have only the necessary permissions. Remove unnecessary privileges promptly to minimize security risks.
Use Multi-Factor Authentication (MFA): Implement MFA for accessing privileged accounts to add an extra layer of security. This helps prevent unauthorized access even if credentials are compromised.
Monitor and Audit Privileged Account Activities: Keep track of privileged account activities through session monitoring and auditing. This helps detect any suspicious behavior or unauthorized access attempts.
Secure Password Management: Enforce strong password policies, regularly rotate passwords, and use password vaults to securely store and manage privileged credentials.
Educate Users on Security Best Practices: Provide training to users on the importance of security practices, such as avoiding sharing credentials, recognizing phishing attempts, and reporting suspicious activities.
By following these best practices, organizations can enhance their security posture, reduce the risks associated with privileged accounts, and ensure the proper management of critical systems and data.
How PAM Is Implemented?
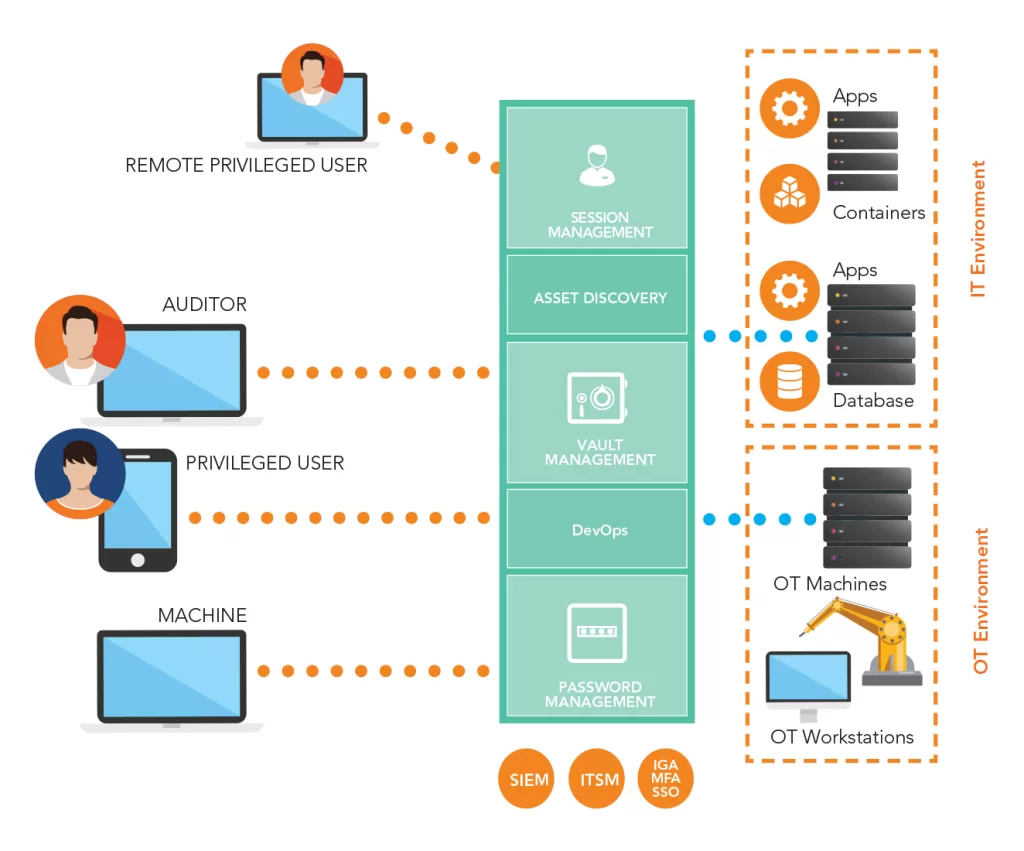
Implementing Privileged Access Management (PAM) involves several steps to ensure the effective control and monitoring of access to critical systems and data. Here are some common steps in implementing PAM:
Assessment and Planning: Begin by assessing the organization’s current privileged account landscape, identifying risks, and defining the scope of the PAM implementation. Develop a comprehensive plan that outlines goals, timelines, and resources needed for successful implementation.
Selecting a PAM Solution: Choose a PAM solution that aligns with the organization’s requirements and offers features such as password management, access control, session monitoring, and privilege elevation. Consider factors like scalability, integration capabilities, and ease of use.
Deployment: Install and configure the chosen PAM solution according to the vendor’s guidelines. Customize the solution to meet the organization’s specific needs, including defining privileged account policies, access controls, and monitoring parameters.
Integration: Integrate the PAM solution with existing systems, applications, and directories to ensure seamless operation and centralized management of privileged accounts. This may involve connecting to Active Directory, LDAP, or other identity management systems.
User Training: Provide training to users, administrators, and IT personnel on how to use the PAM solution effectively. Educate them on best practices for managing privileged accounts, accessing critical systems securely, and responding to security incidents.
Testing and Validation: Conduct thorough testing of the PAM solution to ensure it functions as intended and meets security requirements. Validate the implementation by simulating different scenarios, testing access controls, and verifying monitoring capabilities.
Ongoing Maintenance and Monitoring: Regularly update the PAM solution, review access policies, and monitor privileged account activities for any anomalies or security incidents. Implement continuous improvement processes based on feedback and security assessments.
By following these steps, organizations can successfully implement Privileged Access Management to enhance security, reduce risks associated with privileged accounts, and safeguard critical systems and data.
Privileged Access Management (PAM) Solution Provider
Mechsoft Technologies, a leading provider of Privileged Access Management (PAM) solutions in Dubai, is dedicated to enhancing the security of digital infrastructures across various industries. With a deep understanding of the unique cybersecurity challenges faced by businesses in the region, Mechsoft Technologies offers a comprehensive suite of PAM tools designed to safeguard critical assets from unauthorized access and potential cyber threats.
Our solutions are tailored to meet the specific needs of each client, ensuring robust protection for sensitive data, systems, and networks. By leveraging advanced encryption, multi-factor authentication, and real-time monitoring, Mechsoft Technologies empowers organizations to control and monitor privileged access seamlessly.



