Cyber criminals often target users with ‘Privileged Access’ to an organization’s systems and networks. They are targeted using phishing and social engineering techniques since gaining control over these credentials ensure complete access to the network. Using privileged access management (PAM) prevent all the cyber attacks to your system and networks.
With increasing dependency on outsourced workforce and digital accountability, granting privileged access is becoming critical for many businesses. Privileged Access is a special access granted to specific users – like IT Admins, or personnel who needs to perform administrative tasks or users who need to read or edit sensitive data.
Privileged access management (PAM) helps you maintain control and visibility over your organization’s most critical systems and data. It includes numerous tools and features that can help deter and prevent data breaches caused by both malicious insiders or external cybercriminals.
Also See: What Are The Benefits Of PAM?
A robust PAM solution typically consists of three components:
- Access Manager
- Session Manager
- Password Manager
Together, these modules support your security teams in their efforts to protect your organization from data breaches or other cyber-attacks.
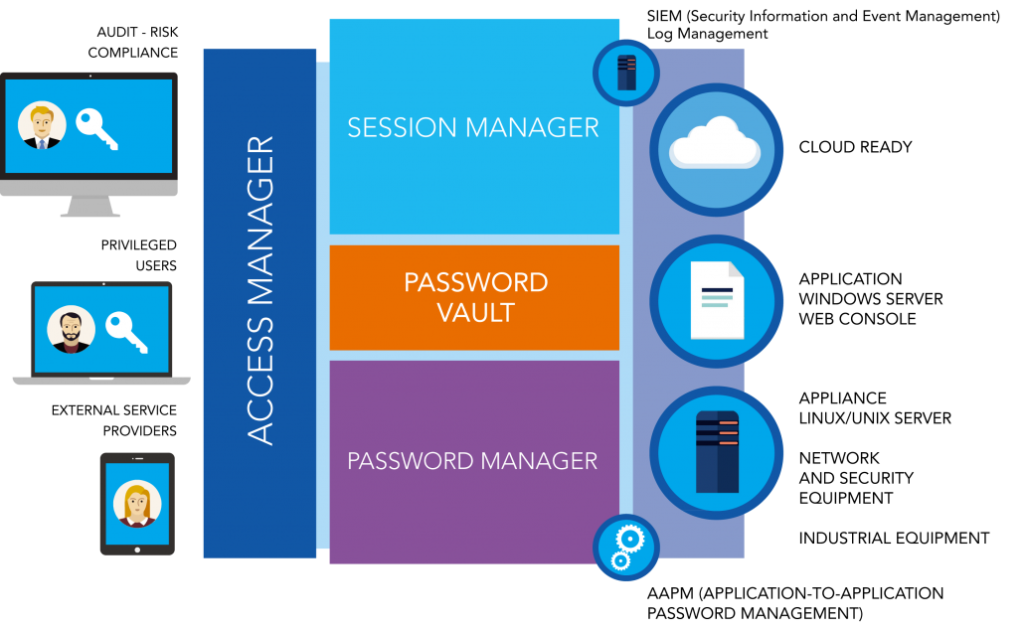
PAM with the WALLIX Bastion
WALLIX provides a complete PAM solution through their Professional and Enterprise Bastion offerings. These Privileged Access Management features support organizations’ security efforts through comprehensive and robust security tools. Easily monitor, control, and audit all the actions of your privileged users in order to detect and prevent breaches before they occur with the WALLIX Bastion.
Discover how WALLIX can help secure your digital future. Connect with Rejoy Radhakrishnan to get your free demo.



