The global pandemic has caused many IT enterprises to be more adaptive to multiple remote access points and permissions for users. New cyber security threats have emerged, and further serious responsibilities have surfaced as a result of the inevitable situation. To ensure uninterrupted functioning, appropriate access must be provided to your privileged users while minimizing risks. Securing privileged accounts is vital to protecting sensitive information and critical systems from cyber attack. Privileged users have access to privileged accounts to maintain your IT infrastructure. The unrestricted access of privileged accounts makes them valuable to cybercriminals.
Need for PAM
Privileged Access Management (PAM) helps organizations protect against the accidental or deliberate abuse of privileged access by streamlining the authorization and monitoring of privileged users.
- 47.7% of data breaches were the result of phishing, potentially caused by users having their credentials compromised
- 9% of breaches were due to employee carelessness, such as error, disposal, or misplacement of data
PAM offers you the ability to control your network by implementing access restrictions, revoking access, and monitoring activities. PAM is made up of three components: an access manager, a session manager, and a password manager.
- Access Manager – allows administrators to view exactly who is accessing systems and data so they can detect vulnerabilities and prevent threats.
- Session Manager – helps administrators control access to system in real time.
- Password Manager – supports the implementation of password best practices and ensures all passwords are encrypted in a secure vault.
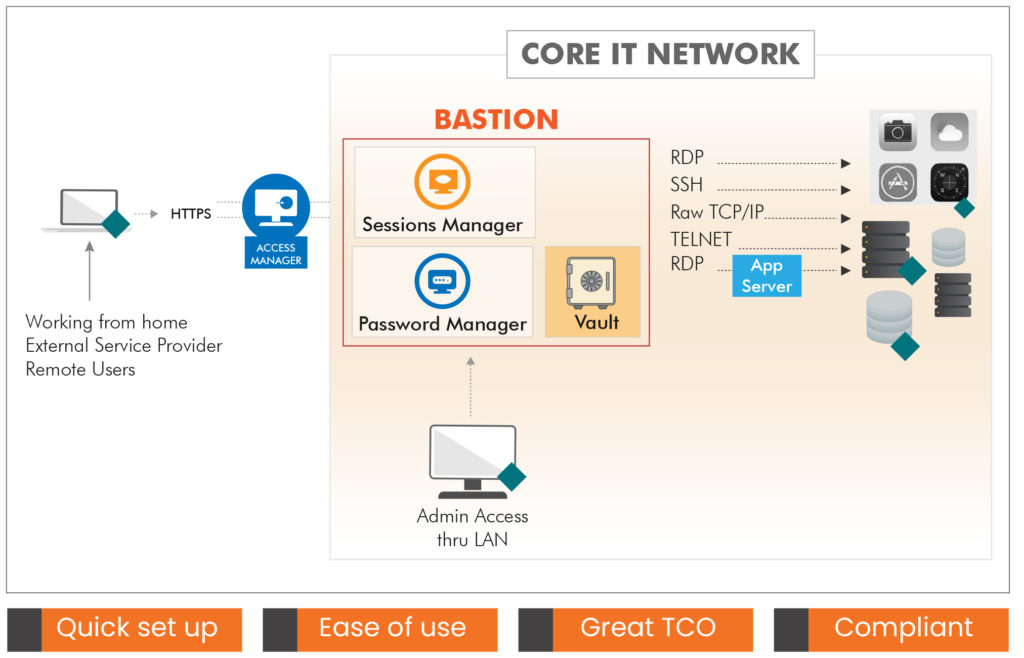
The WALLIX Bastion Privileged Access Management Solution provides a complete and robust PAM solution.
The WALLIX Bastion is an all in one certified Privileged Access Management platform
- Audit & Compliance
- Cyber attacks and Internal Threats
- Third-Party Monitoring and Remote Control
Benefits of the WALLIX Bastion Elected “Best Buy” by SC Magazine
- All-in-one certified solution
- Complete visibility
- Guaranteed user adoption
- Unobtrusive & rapid deployment
Try the WALLIX Bastion for free and explore the benefits. Connect with Rejoy Radhakrishnan to get your free demo.
Mail: rejoy@mechsoftme.com
Phone: +971 52 490 8692



